An authentication proxy, which is used for remote access, might use your identity provider to authenticate users. The authentication proxy will challenge the user before visiting the Appshare PWA and customer services. The authenticated state is usually maintained through http-only cookies. The cookies are set by the authentication proxy and the Appshare PWA is not aware of them. By default, a cookie is only sent by the browser to the same domain it was set by. This requires the Appshare PWA hosting service and customer service to be on the same domain.
Appshare PWA can not use the authenticated state from the authentication proxy to sent access tokens to the customer service. Appshare PWA can still leverage the authenticated state on the identity provider to request an access token without the user providing credentials again.
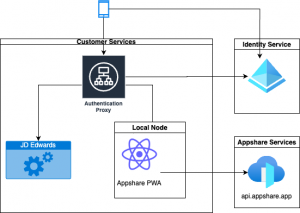
The browser needs to maintain sessions with the following services.
- Load balanced authentication proxy (all requests are matched against a domain state inside the Load balanced)
- Identity Provider
- Customer service with session / JD Edwards AIS
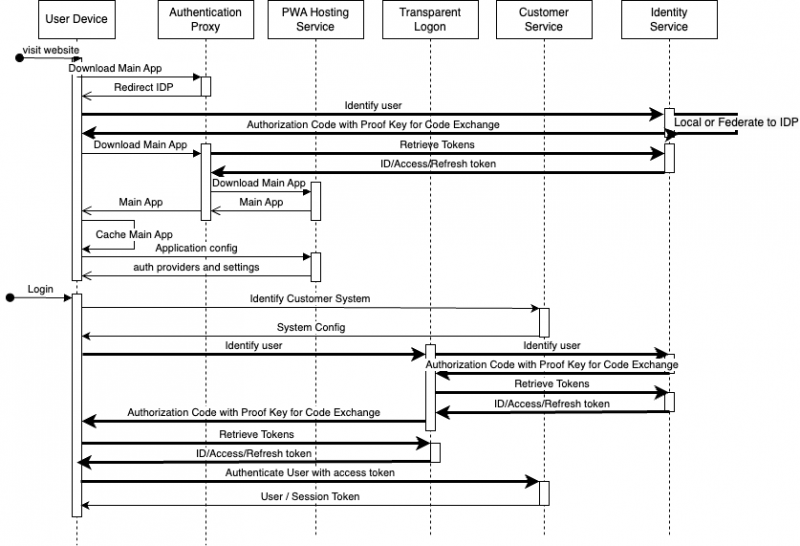
- The user visits the website where appshare is hosted
- The Authentication proxy redirects the user to the identity provider
- User provides credentials to the identity provider
- The identity provider redirects the user to the Authentication proxy with an Authorization Code
- The Authentication proxy retrieves from the identity provider the tokens based on the Authorization Code
- The Authentication proxy creates an authenticated state based on the tokens
- The PWA Main app is downloaded from the hosting service and caches it on the device for future use.
- The PWA loads the application configuration for identity providers
- The PWA shows the Login to the user
- The user logs into the Appshare PWA by entering in the server and selecting the identity provider
- The PWA from the device requests system information from the customer server to identify which features are available
- The PWA redirect the user to the identity providers and receives an Authorization Code
- The PWA retrieves from the identity provider the tokens based on the Authorization Code
- The PWA authenticates the user through the customer identity service with the token received from the external identity provider (For JD Edwards this is the AIS tokenrequest)
