Starting with Tools Release 9.2.5.4, you can use JWT (JSON Web Token) to access the EnterpriseOne Web Client and Orchestrator Studio. Transparent Logon can produce a JWT to access JD Edwards. Transparent logon requres a private key to sign the JWT. JD Edwards must be configured to use the public key to trust the JWT. There are a few steps to configure this
- Generate a public private key pair
- Upload the private key to Transparent logon
- Configure JD Edwards Single Sign On with a JSON Web Token by uploading a truststore with the public key (wrapped in a certificate)
Generating Your Private Key
openssl genrsa -out yourdomain.key 2048
openssl pkey -in yourdomain.key -out yourdomain-pkcs8.key
Upload this file in transparent login
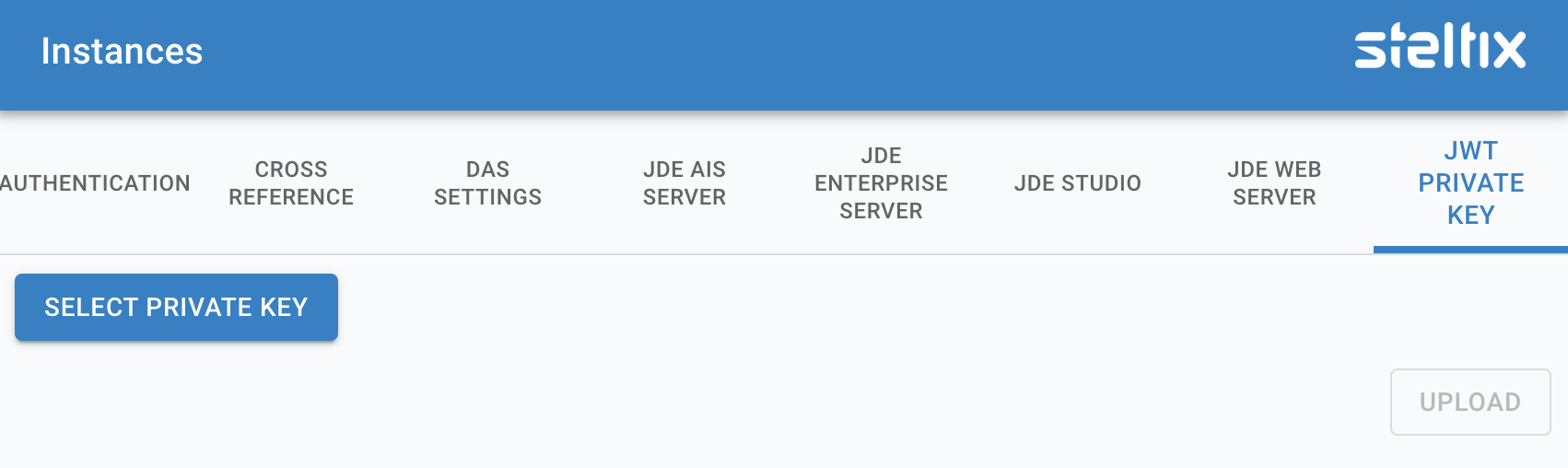
Upload JWT into TL
Select the Select Private Key button and navigate to your key file you just generated. Then use the upload button to load the file into your TL server.
When a Private Key has been applied, you will see this in this screen as follows:
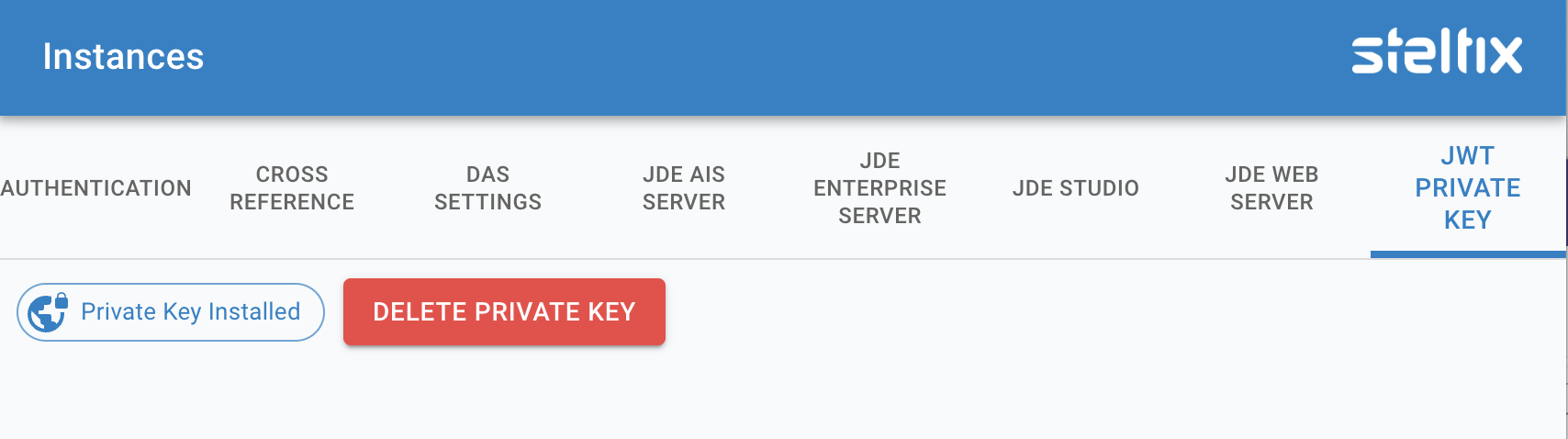
Certificate applied
Use the button to delete the private key.
Create certificate for JDEdwards
A trsutstore for JDEdwards is a java keystore which only contains a certificate entry with the public key. To create such a truststore we need to wrap the public key in a self-signed certificate. A self-signed certificate is a certificate that’s signed with its own private key. This requires to create a Certificate Signing Request and then create the certificate by signing the request.
Ue the following command
openssl req -key yourdomain.key -new -x509 -days 365 -out yourdomain.crt
The -days option specifies the number of days that the certificate will be valid.
Follow the instructions to import this certificate into JDEdwards
Make sure you configure the “External OAuth JWT Trust Configuration” and not the “AIS Internal JWT Trust Configuration for Authentication”
