Single Sign on for JD Edwards made extremely easy.
Transparent Logon provides a simple, straightforward and secure way of allowing your users to access JD Edwards without having to enter a password, provided they are an active and authenticated user in your Windows domain, or can be authenticated using a OpenID/OAuth/SAML2 provider (Office365 and Fortigate are being used but any provider should work)). Available for immediate download from https://www.steltix.com/tl and up and running in minutes.
Technical Concept
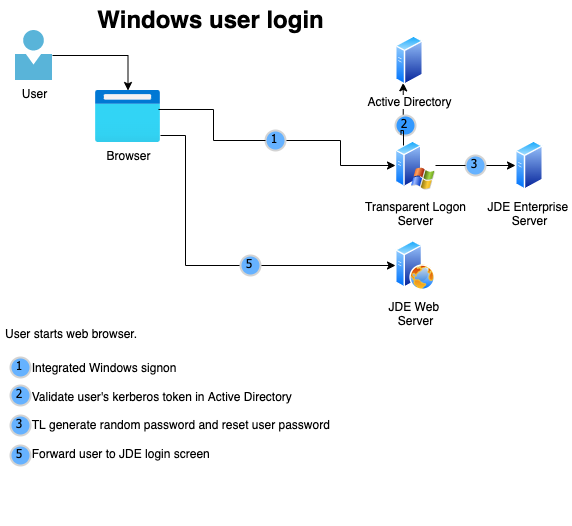
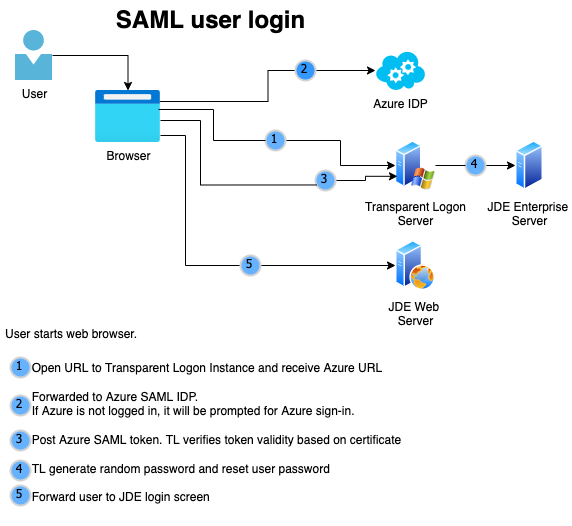
The main steps by the transparent logon server are:
- Identify the user through
- windows domain authentication
- Federation with SAML2 with a identity provider
- Federation with OpenID Connect with a identity provider
- Create credentials which JDEdwards understand
- Set the user password to a random value
- Generate a JSON Web Token
- Redirect the user with the new credentials
Transparent Logon installs a webserver for each environment it needs to serve. Every server runs on the same machine as an instance on a separate port.
Transparent Logon URL’s
Once you install a transparent logon server, you can create separate server instances to serve your environments. The URL your users use on this server defines the action Transparent Logon is taking. That is essentially what provides them with Single Sign On for JD Edwards.
Administrator Access
Syntax:
<TLServer>:8080/admin/
When accessing the admin interface the administrative back ends opens. Make sure to restrict access to the panel by setting the correct windows group. Initially, access in not secured, but after uploading a certificate, access to the admin panel is through https.
User Access
Syntax:
<TLServer>:<Port>/<url>
The URL for end-user to use when interacting with the system served by Transparent logon contains a portnumber and a parameter.
The port is defined by the instance and usually relates to a specific JDEdwards environment.
The parameter defines the actual service the user needs to be redirected to as follows:
- /jde:
When navigating to /jde, TL will navigate to the JD Edwards logon screen (of the server served by this instance of TL) and automatically try to logon. When that is not possible (due to a missing cross reference for instance) it will simply present the logon screen.
When one Windows user has multiple JDEdwards users associated, TL will first prompt for tje JDEdwards user to use. - /tl:
Alias for /jde. - /das:
Identical as the above, but now TL will create a user session in DAS’s Reports Now. - /studio
Identical as the above, but now TL will create a user session in the Orchestrator Studio Now. - /email:
TL will now rest the JDEdwards password of the user id correlated to the windows user id and sent a reset mail to the user.
This requires correct setup of email section and the existence of an email address in the cross reference database. - /jderest:
Used for token requests and AIS-API calls into JDEdwards. - /whoami:
Used to check the JDEdwars user id(s) correlated to your windows username.
